03 Aug
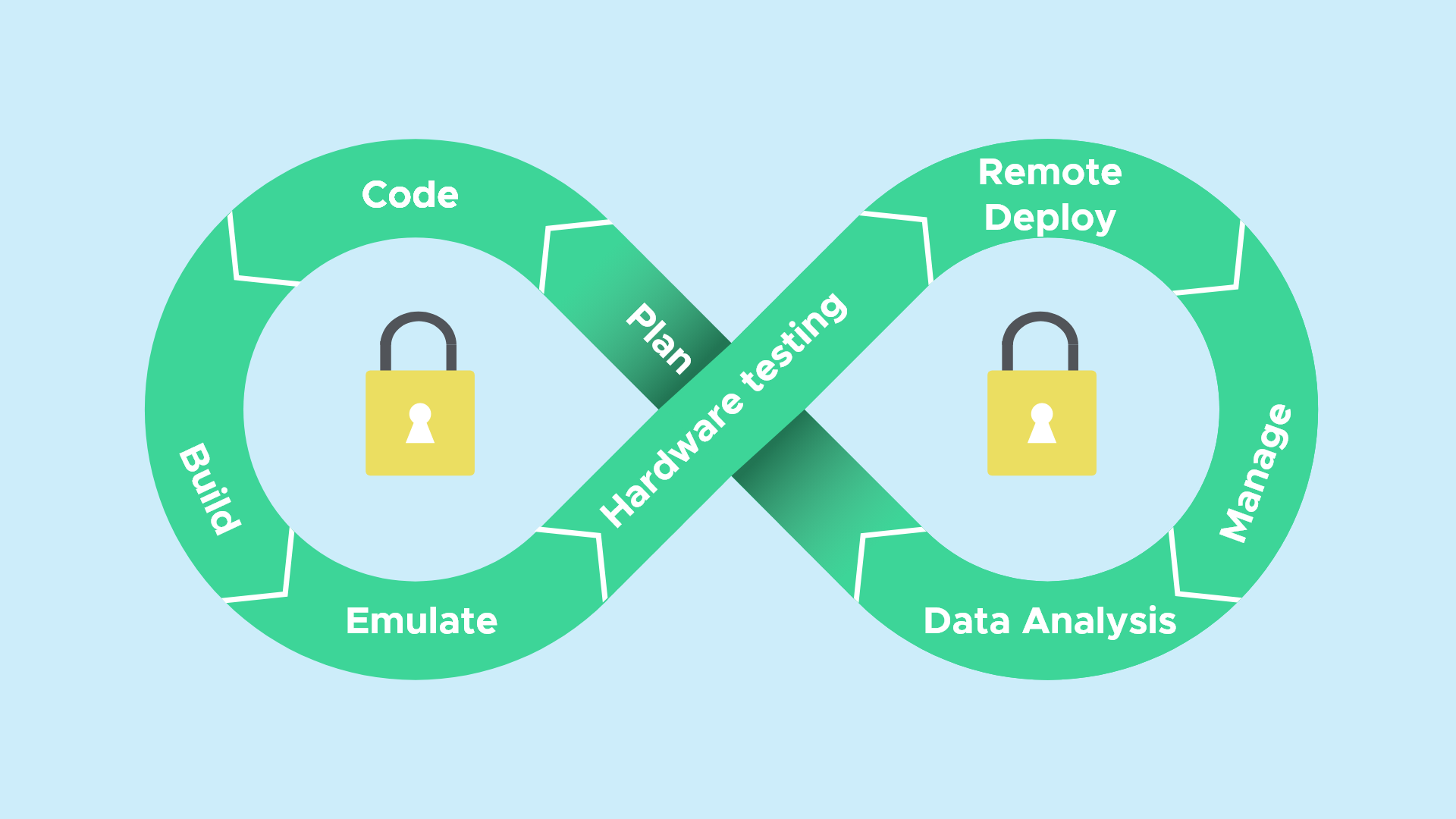
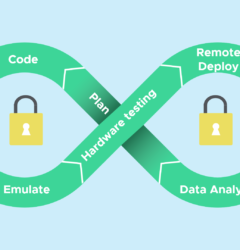
Embedded DevOps is a developing practice used by embedded engineers around the world. DevOps originally started within software development, allowing web app developers or mobile developers to quickly check code and push updates out rapidly, even when working in a team of hundreds of engineers.
Since then, the Internet of Things (IoT) and the rise of edge computing has taken the embedded industry by storm. Embedded systems are not just small offline microprocessors designed to perform simple tasks. They are now consistently feeding information to connected servers as well as receiving updates.
In fact, so much data is now collected that there is now demand for devices to analysis data at the same location it is collected. By doing so latency, bandwidth and storage needs are reduced which provides time and cost savings.
This new connectivity, however, opens our embedded devices to a range of new security threats. In this article, we will provide a brief overview of some of these threats as well as how proper security practices in embedded DevOps can mitigate these risks.
Malware attacks
In late 2016, the French telecom company OVH was hit by a distributed denial-of-service (DDoS) attack that was estimated to be 100 times larger than similar threats. The culprit was a piece of malware known as the Mirai botnet.
Technically malware is any type of malicious software that tries to gain access and take control of a device. Botnets are a specific type of malware that essentially creates a network of infected computers that can then be controlled from a singular point.
What made the Mirai botnet so effective is that instead of targeting computers, it targeted IoT devices and breached their security by trying a list of default usernames and passwords.
Data breaches
A data breach is when sensitive or confidential data is copied, transmitted or stolen by unauthorised individuals. IoT devices present a new vector for data breaches. Perhaps one of the most famous takes was the Verkada hack in March 2021.
Attackers gained access to Verkada, a cloud-based video surveillance company. They gained access to over 150,000 company cameras, including those at Tesla factories and warehouses.
They managed to do so by gaining access to a customer support server and then taking administrator credentials to log into a customer support web interface. Using those credentials, they were then able to access the connected cameras
Physical Attacks
Sometimes even unconnected devices can present a security problem. Attackers with physical access to embedded systems can perform hacks and analysis that cannot be done over the internet.
One classic example is firmware extraction. This is where the firmware that the embedded system is stolen and analysed to gain access to sensitive data, such as cryptographic keys. There are many videos on YouTube showing insecure iot devices being vulnerable to these attacks.
By having access to IoT devices attackers can leverage insecure debug interfaces to gain access to local shells, such as UART or JTAG.
They can also read directly from flash memory. Often flash chips are desoldered from the board and are extracted using suitable readers.
How embedded DevOps can help to improve security
At Beetlebox, we believe strongly that a strong embedded DevOps within a company can help lower the risk of security. In fact, if you are interested in learning more about how we can help secure your embedded systems, you can talk to one of our experts. Here is how we use embedded DevOps to improve by security.
Security By Design
The first way that DevOps can protect against these vulnerabilities is a cultural shift from security being an afterthought to security by design.
At every point it is important to consider where the vulnerabilities lie and how these risks will be mitigated early on, before they become a problem. Set benchmarks in the requirements process that must be meet before a job is considered finished.
Integrate Security Testing with embedded DevOps
Throughout the development process, embedded DevOps can be used to create automated security tests that check the latest firmware against common vulnerabilities. Some basic automated tests that would have stopped the examples from above are:
- Strong password securing every interface.
- Testing for default passwords or weak passwords.
- Checking administrative privileges and defining users for each embedded device.
Embedded DevOps stops exploits or bugs before they become a problem
Simply put non-functioning and buggy code presents a security risk to organisations. The Verkada breach was caused by an unpatched customer support server. If the fault had been found before the server was released the attack may not have occurred.
Embedded DevOps is a practise that is devoted to finding bugs early in the development process before they become a problem and risk the reputation of the company.
Conclusion
Through security by design, integrating security testing and implementing functional testing to stop vulnerabilities, embedded DevOps provides a powerful basis for lowering the risk of security vulnerabilities.
As we have seen in numerous examples the challenges of IoT devices include malware, data breaches and even physical extracting data from the device. By ignoring these risks companies open themselves up to reputational damage as well as risk of litigation against them.